The evolution of internet security has become a pressing concern for both individuals and organizations alike. As we continue to navigate an increasingly digital world, the need for secure communication channels is paramount. One such channel that has emerged in this context is the S-HTTP protocol, which stands for Secure Hypertext Transfer Protocol. Unlike its more popular counterpart, HTTPS, S-HTTP offers a distinct method of ensuring the confidentiality and integrity of data as it travels across networks.
In an age where cyber threats loom large, understanding the intricacies of protocols like S-HTTP is essential. This article will delve into the features, advantages, and operational mechanisms of the S-HTTP protocol, offering a comprehensive overview for those interested in enhancing their knowledge of online security. Whether you are a tech enthusiast or a professional in the field, this exploration will provide valuable insights into how S-HTTP functions and its significance in today's digital landscape.
As we explore the S-HTTP protocol, we will address several key questions that often arise regarding its implementation and efficacy. From its historical context to its practical applications, this article aims to present a well-rounded perspective on S-HTTP and its role in securing internet communications. Join us as we embark on this informative journey through the world of S-HTTP.
What is the S-HTTP Protocol?
The S-HTTP protocol is designed to provide a secure communication framework for transmitting data over the internet. It operates in conjunction with the traditional HTTP protocol, offering an additional layer of security by encrypting the data being transmitted. This encryption ensures that sensitive information, such as passwords and personal details, remains protected from unauthorized access during transmission.
How Does S-HTTP Work?
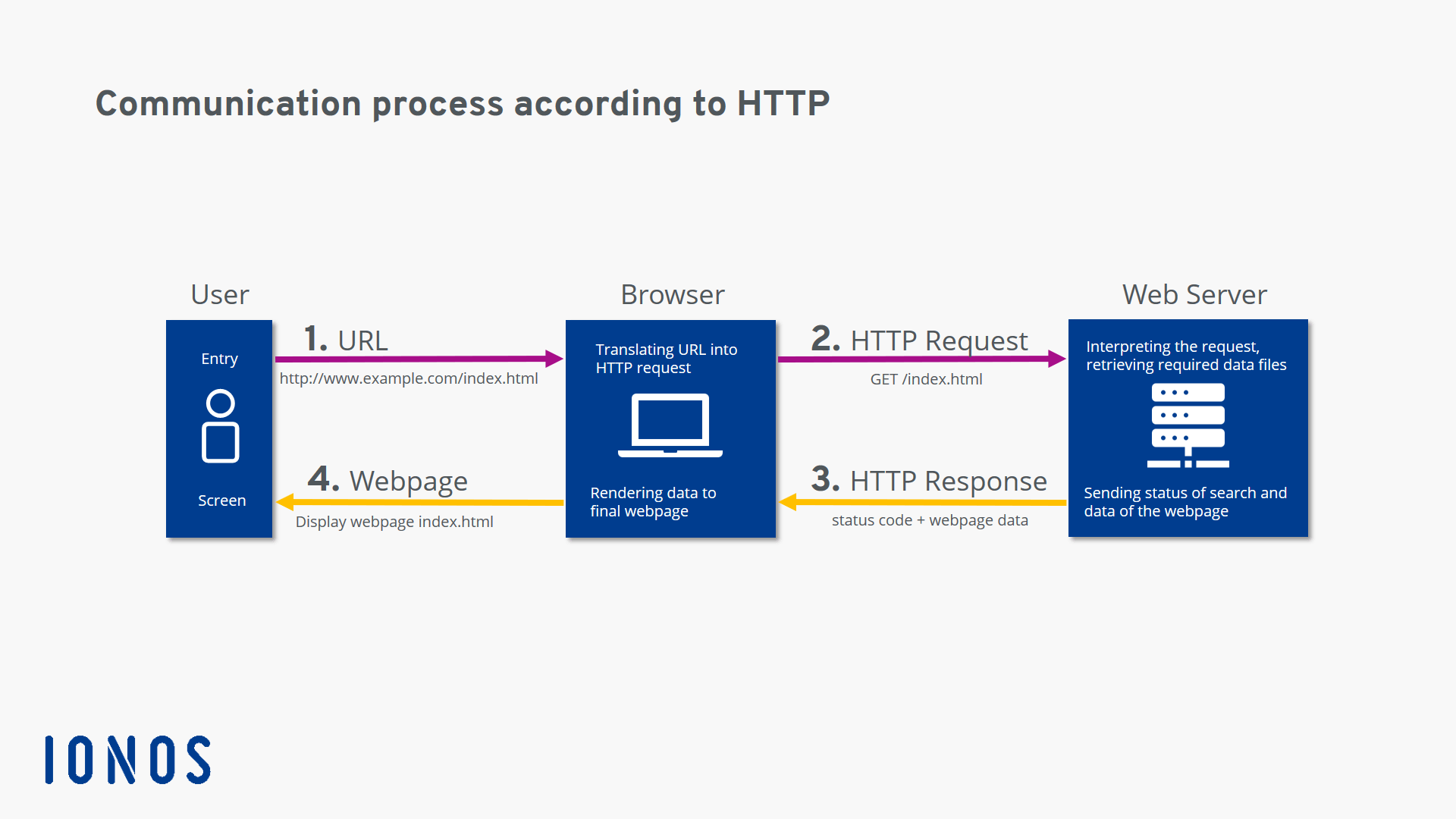
At its core, the S-HTTP protocol operates by using encryption algorithms to secure the data being sent between a client and a server. When a client makes a request to a server using S-HTTP, the following steps typically occur:
- The client initiates a connection to the server using the S-HTTP protocol.
- The server responds with its public key, which the client uses to encrypt the request.
- The encrypted request is sent to the server, which decrypts it using its private key.
- The server processes the request and sends back the response, also encrypted for security.
- The client decrypts the server's response using the server's public key.
What are the Advantages of S-HTTP?
S-HTTP offers several key advantages that make it a valuable tool for secure communication:
- Data Integrity: Ensures that the data sent has not been altered during transmission.
- Confidentiality: Encrypts data to protect sensitive information from prying eyes.
- Authentication: Verifies the identity of the parties involved in the communication.
- Compatibility: Can be implemented alongside existing HTTP infrastructure.
Is S-HTTP Still Relevant Today?
While S-HTTP was a significant innovation in its time, its relevance in today's internet landscape is often debated. With the rise of HTTPS as the dominant protocol for secure web communications, many wonder whether S-HTTP is still utilized. However, it remains an important part of internet history and provides valuable lessons in the development of secure communication protocols.
How Does S-HTTP Compare to HTTPS?
To understand the standing of S-HTTP, it is essential to compare it with HTTPS:
- HTTPS: Utilizes SSL/TLS protocols to provide security and has become the standard for secure web communications.
- S-HTTP: Focuses on encrypting individual messages rather than establishing a secure channel for all communications.
While HTTPS is more widely adopted due to its comprehensive approach to security, S-HTTP's message-oriented security model still holds relevance in certain contexts.
Who Uses the S-HTTP Protocol?
The S-HTTP protocol is not as commonly used as HTTPS, but it can still find its place in specific scenarios where message-level security is required. Industries that prioritize high security, such as financial services and healthcare, may still implement S-HTTP for certain applications. Additionally, legacy systems that were built around S-HTTP may continue to use this protocol for compatibility reasons.
Conclusion: The Legacy of S-HTTP
In conclusion, the S-HTTP protocol serves as a reminder of the ongoing evolution of internet security. While it may not be the go-to choice for secure communications today, understanding its principles and applications provides valuable insights into the development of modern security protocols. As we continue to navigate an increasingly interconnected world, the lessons learned from S-HTTP will undoubtedly inform the future of secure data transmission.
Exploring the fundamentals of the S-HTTP protocol not only enhances our understanding of internet security but also emphasizes the importance of safeguarding our online interactions. As the digital landscape evolves, so too must our approaches to security, ensuring that protocols like S-HTTP are not forgotten but rather integrated into a broader understanding of how to secure our data in the digital age.
You Might Also Like
Ebrahim Meaning: Unveiling The Essence Of A NameExploring The Journey Of Starter Pokémon Final Evolutions
Unveiling The Truth: Dutch Bros Nitro Cold Brew Calories
Experience A Feast: Golden Corral Open On Thanksgiving
Discover The Best Ways To Baixar Filmes Torrent Grátis
Article Recommendations
- Chloea Surreal A Dive Into Her Artistic World
- Fabio Ochoa Fortuna A Journey Of Influence And Impact
- Exploring The Life Of Robert Plants Wife A Journey Through Love Music And Legacy